Using the concrete example of the relocation of an HR analytics application to a cloud environment, some special features of cloud computing in the BI environment are presented here.
EXPERIENCES FROM THE IT OUTSOURCING BUSINESS PAVE THE WAY TO THE CLOUD
Cloud computing has complemented the IT sourcing initiatives in recent years. The services in the cloud offer customers more opportunities. You order very promptly and pay according to the originator. These services were planned in classic outsourcing, but were offered relatively rigidly. As part of the cloud computing measures, small services are now being cut very flexibly and made available very quickly. Flexibility, scalability, cost transparency, multi-cloud strategy and exit strategy represent real added value. However, the necessary expansion or adaptation of the IT strategy and the pressure to change the IT infrastructure and IT planning are no less sustainable under the cloud sign than in traditional sourcing.
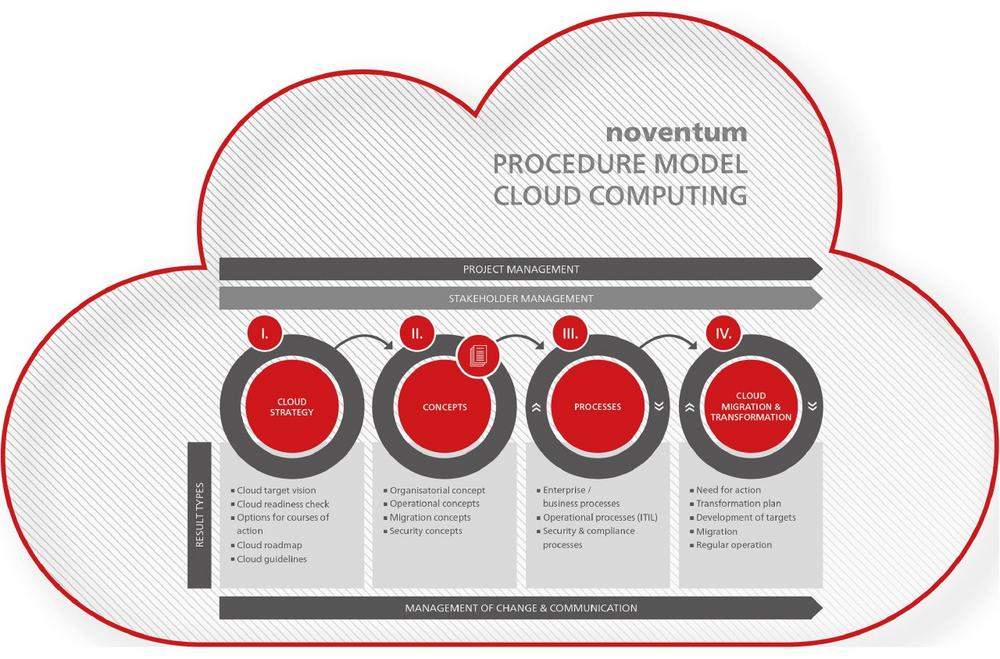
Orientation towards a well thought process model creates clarity on the path to the cloud. If this is to become a safe and successful next step in the history of corporate IT, some important aspects need to be considered.
DATA WAREHOUSE ARCHITECTURE IN THE CLOUD: A TECHNICAL BI TARGET ARCHITECTURE
In the cloud strategy phase, a technical target architecture will be developed. Figure 2 of a BI application HR Analytics shows how a classic data warehouse architecture in layered architecture and SAP integration, versioning, and alternative frontend options can be positioned at the interface of enterprise IT and cloud. Essential components of the enterprise BI architecture are mapped in the cloud, but some central components such as the SAP database and core processes remain in the enterprise.
MIGRATION OF THE DEVELOPMENT ENVIRONMENT – A TECHNICAL CONSIDERATION
Complex applications with different layers (development, data, application) are often built on a single system. This seems pragmatic in the pilot and development phase. Before commissioning, however, it is also a question of system security to think about gradual distribution to different systems. The moment of transition to the cloud is such a time. Our example illustrates some of the solution approaches that arise when migrating or deploying the cloud architecture.
• The existing system was sorted by functions and transferred to several systems. The separation enables better protection against interference. Subsystems that contain databases and do not require public IP addresses have been separated.
• The environment is managed separately according to infrastructure responsibility. The Cloud Architects use the AWS Management Console to manage the infrastructure in the cloud and the regulatory framework for network communication. It is important that you do not have access to the contents of the systems.
• The system layer is managed by BI team administrators, who in turn have no access to the cloud presence infrastructure.
ARCHITECTURE IN THE CLOUD
The conceptual design of the cloud architecture raises various topics, some of which are presented in the case study:
Network design:
• 2 Tier model – one subnet for each of the systems that contain program logic and processing (public subnet) and another for the systems that hold the data (private subnet).
• For the communication of the systems from the private subnet, a NAT instance is available in the public subnet.
• None of the systems can be accessed directly from the Internet; if necessary, external communication is possible if initiated internally.
• Internet access has been disabled, but can be enabled as an option. Our example HR-Analytics communicates from a private subnet in AWS via the VPN tunnel with the source system SAP HCM or Persis on the OnPremise side.
The connection to the cloud infrastructure is made via a VPN tunnel. This is safer than a pure Internet connection and cheaper than a dedicated line:
• Site to site connection, virtual Astaro on OnPremise side connected to the VPC-VPN service on AWS side (the VPN tunnel is currently one of the best ways to secure traffic between networks).
• Unlike End to End, no additional software is required on the end devices. The tunnel is implemented between the network gateways.
In addition to the classic installation, the SQL Server was also provided as a PaaS service via AWS RDS (Relational Database Service) and thus the administration of patches, backups etc. was transferred to the service.
For authentication against the cloud infrastructure, a multi-factor authentication is recommended to secure administrative access for the AWS infrastructure. This offers a much higher level of security than the user and password alone.
MOTIVATION AND OBJECTIVES
In the cloud strategy phase, there is also the need to perform a cloud readiness check and set guidelines for the cloud. In addition to an assessment of the current situation and a maturity analysis of infrastructure, processes and skills, the question of regulatory framework conditions and data classification is particularly relevant.
HR applications in particular are subject to the critical question of data protection …
Read the complete article on novum online, the Information platform of noventum consulting.
noventum consulting GmbH is an international IT management consultancy.
Founded in 1996 in Münster, today noventum is represented in Münster and Düsseldorf with more than 100 employees. Independent noventum partner companies work in Istanbul and Luxembourg.
The managing partner is Uwe Rotermund.
noventum consulting supports its customers in their IT challenges and in their efforts for a modern corporate culture.
Customers are predominantly DAX companies as well as medium-sized companies and organizations with a large IT infrastructure.
noventum consulting GmbH
Münsterstraße 111
48155 Münster
Telefon: +49 (2506) 9302-0
Telefax: +49 (2506) 9302-23
http://www.noventum.de
MicroStrategy Lead
Telefon: +49 (2506) 93020
Presse
Telefon: +49 (2506) 9302-0
E-Mail: matthias.rensing@noventum.de
![]()